Integration via Wiegand
The Wiegand feature enables the Akuvox device to act as a controller or a card reader.
Set it up on the Device > Wiegand > Wiegand interface.
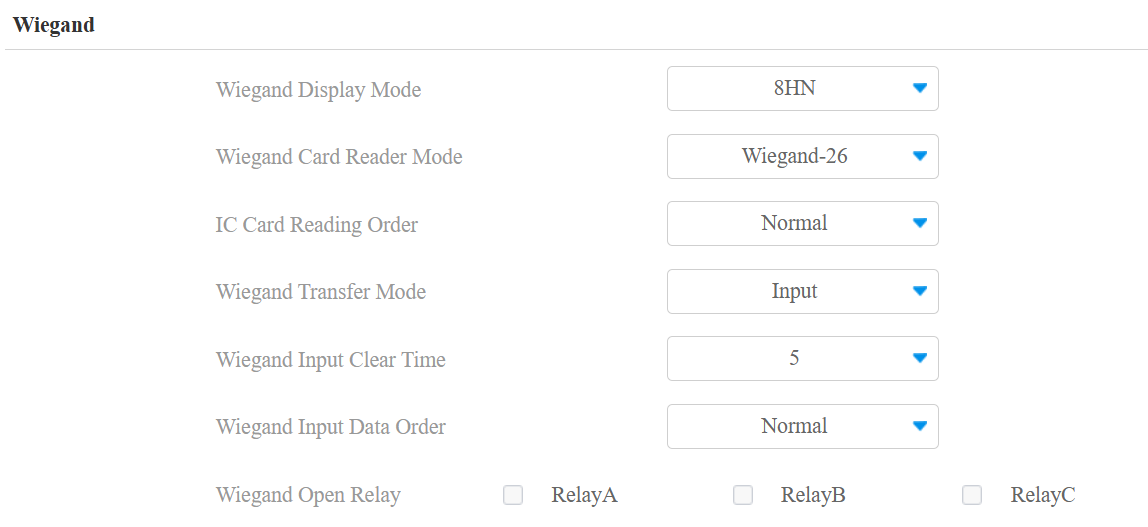
Wiegand Display Mode: Select the Wiegand card code format from the provided options.
Ignore Facility Code: This option is available when 6H3D5D(WG26) is selected. When enabled, the first three bits of the cards will be ignored for successful card reading.
Wiegand Card Reader Mode: The transmission format should be identical between the door phone and the third-party device. It is Wiegand-26 by default.
IC Card Reading Order: This option only works when Wiegand-26 is selected.
Normal: The device will read the last three bytes of the IC card. For example, if the IC card number is 840C9F50, 0C9F50 will be read.
Reversed: The device will read the first three bytes of the IC card. For example, if the IC card number is 840C9F50, 840C9F will be read.
Wiegand Transfer Mode:
Input: The device serves as a receiver.
Wiegand Input Clear Time: When the interval of entering passwords exceeds the time. All entered passwords will be cleared.
Wiegand Input Data Order: Set the Wiegand input data sequence between Normal and Reversed. If you select Reversed, then the input card number will be reversed.
Output: The device serves as a sender. If users can only open the door by swiping an RF card, select the Wiegand transfer mode as Output.
Wiegand Output Basic Data Order: Set the sequence of the card data before going through the Wiegand conversion and outputting the card code.
For example, if the card data is 0x11 0x22 0x33 0x44 and the Reversed option is selected, the data will be 0x44 0x33 0x22 0x11.
Wiegand Output Data Order: Determine the sequence of the card data after the Wiegand conversion.
For example, if the card data is 0x11 0x22 0x33 0x44 0x55, it will be 0x33 0x44 0x55 after the Wiegand conversion(e.g., Wiegand 26). If Reversed is selected, the card data is 0x55 0x44 0x33.
Wiegand Output CRC: It is enabled by default for Wiegand data inspection. Disabling it may lead to integration failure with third-party devices.
RF Card/PIN/QR Code Verification: When enabled, the device will verify whether the credential is assigned to a user. If it is not, a prompt "Opening Door Failed" will pop up on the door phone screen. When disabled, the door phone will not perform local verification.
Convert To Card No. Output: The device serves as a sender. If users are assigned multiple door-opening methods, select the Wiegand transfer mode as Convert To Card No. Output.
Wiegand Open Relay: Check the relay to be triggered through Wiegand.
When the device is in Wiegand Output mode, you can set the Wiegand PIN code output format that determines how data is transmitted. The format should be consistent with that of the third-party device.
Set it up on the Device > Wiegand > Convert To Wiegand Output interface.

8 bits per digit: When users press "1" on the keypad, the binary data will be transmitted in 8 bits, "11100001".
4 bits per digit: When users press "1" on the keypad, the binary data will be transmitted in 4 bits, "0001".
All at once: After users enter the whole PIN code, the data will be transmitted according to the Wiegand card reader mode.
Note
Click here to view more information on Wiegand settings including:
Akuvox devices work as Wiegand input/output;
Wiegand Card Reader Connection.
Facility Code Setting
A facility code is a unique number in access control cards. It identifies the device that issued the card.
When the Wiegand Transfer Mode is Output, you can set up the facility code on the Device > Wiegand interface.

Facility Code: The value ranges from 0 to 255. If filled in, the first two digits of the card number will be replaced by the code. If the code is less than 2 digits, a zero will be automatically added to the card number.
Tip
Since the Facility Code replaces the first two digits of the original card number, to keep the original card number intact, you can manually configure the Wiegand Card Reader Mode.
For example, if the card number is 3 bytes (Wiegand-26), you can select Wiegand-34 (4 bytes) to ensure the Facility Code replaces the first two digits with 0 instead of the original number.
Integration via HTTP API
HTTP API is designed to achieve a network-based integration between the third-party device and the Akuvox device.
Set it up on the web Setting > HTTP API interface.
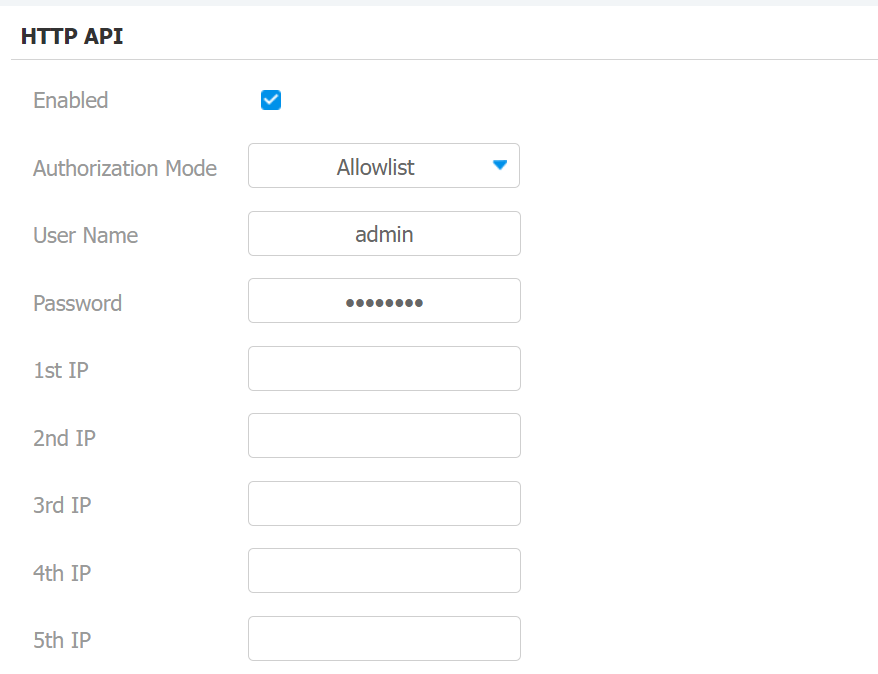
Enabled: Enable or disable the HTTP API function for third-party integration. If the function is disabled, any request to initiate the integration will be denied and return HTTP 403 forbidden status.
Authorization Mode: Select among the following options: None, Normal, Allowlist, Basic, Digest, and Token for authorization type, which will be explained in detail in the following chart.
User Name: Enter the user name when Basic or Digest authorization mode is selected. The default username is admin.
Password: Enter the password when Basic or Digest authorization mode is selected. The default password is admin.
1st IP-5th IP: Enter the IP address of the third-party devices when the Allowlist authorization is selected for the integration.
Please refer to the following description for the authentication mode:
NO. | Authorization Mode | Description |
|---|---|---|
1 | None | No authentication is required for HTTP API, as it is only used for demo testing. |
2 | Normal | This mode is used by Akuvox developers only. |
3 | Allowlist | If this mode is selected, you are only required to fill in the IP address of the third-party device for the authentication. The allowlist is suitable for operation in the LAN. |
4 | Basic | If this mode is selected, you are required to fill in the username and password for the authentication. In the Authorization field of the HTTP request header, use the Base64 encode method to encode of username and password. |
5 | Digest | The password encryption method only supports MD5. MD5( Message-Digest Algorithm) In the Authorization field of HTTP request header: WWW-Authenticate: Digest realm="HTTPAPI",qop="auth,auth-int",nonce="xx", opaque="xx". |
6 | Token | This mode is used by Akuvox developers only. |
Integration with Third-party Access Control Server
The device can transmit QR code and card data to a third-party server without doing any verification. The generation and verification of the data are conducted on the third-party server.
Set it up on the Access Control > Relay > Third-party Integration interface.
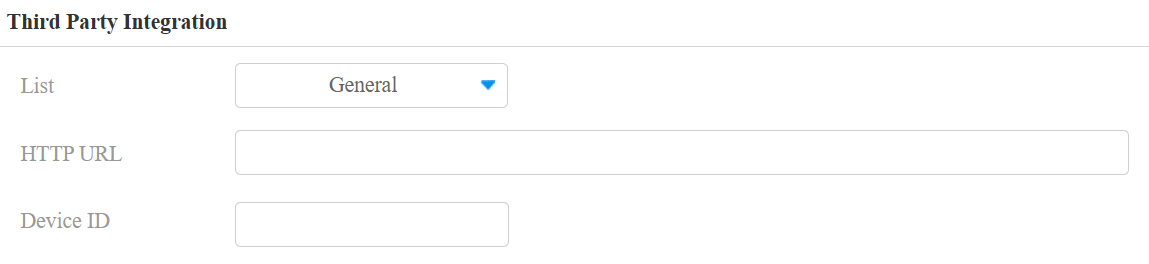
List:
None: Disable the feature.
General: Transmit the QR code-linked HTTP URL in Akuvox’s method.
HTTP URL: Enter the HTTP command format provided by the third-party service provider. After scanning the QR code, the HTTP command will carry the dynamic QR code information automatically before it is sent to the QR code server for verification. See the example: http://{Server IP}:8090/api/visitor/scan?codeKey={QRCode}&deviceId={DeviceID}.
Device ID: The device ID is provided by the third-party server. It will be added to the HTTP command automatically when using a QR code for door access.
Customize: Transmit QR code, RF card, face data, and/or PIN in a customized method.
Prompt on LCD: Select Default to adopt the Akuvox door phone’s door-opening prompt; Select Return Value to use the return value from the third-party server as the prompt.
Remote Verification: Check the access method to be verified by the third-party server. When Face is checked, the face data will be converted into feature values and sent to the third-party server in a string format.
HTTP URL: Enter the HTTP command format provided by the third-party service provider. After scanning the QR code, swiping the card, entering the PIN code, or going through the facial recognition, the HTTP command will carry the dynamic information automatically before it is sent to the server for verification. See the example: http://{Server IP}:8090/api/visitor/scan?codeKey={QRCode}/{CardCode}/{PINCode}/{FaceData}&deviceId={DeviceID}. For example, if a user enters the PIN code, the URL will be http://192.168.35.123:8090/api/visitor/scan?codeKey={QRCode}/{CardCode}/123456/{FaceData}&deviceId=1.
Device ID: The device ID is provided by the third-party server. It will be added to the HTTP command automatically when using QR code/RF card/PIN/facial recognition for door access.
Integration via RS485
You can connect the device to an external device such as SR01 or an OSDP-based card reader via RS485. To make the connection effective, you need to select the right RS485 mode.
Click here to view the detailed configuration of the OSDP feature.
Set it up on the Device > RS485 interface.
Disabled: The RS485 function is disabled.
Others: Select it when the device works with the security relay(SR01).
OSDP: The device is connected to an OSDP-based external device, such as a card reader.
Transfer Mode: Select the RS485 working mode, Output, or Input.
When Output is selected, configure the following options:
Local Relay Verification: Set whether to carry out the access credentials verification. When unchecked, door-opening failure prompts will not be given.
Encryption: Check this option when the protocol is encrypted.
Encryption Key: When it is filled, OSDP will use this value for encryption, employing a customized protocol for communication; When it is left empty, OSDP will use the default encrypted protocol for communication. It must be 32 bits long and can include numbers (0-9) and letters (a-f, A-F).
When Input is selected, configure the following options:
Scan for Readers: Click Scan to detect the connected card reader.
Encryption: Check this option when the OSDP protocol is encrypted.
Encryption Key: Fill in the key when Encryption is checked. If the output device is a third-party card reader, please confirm the key with the service provider.
Modify Key: Click to modify the encryption key, which must be 32 bits long and can include numbers (0-9) and letters (a-f, A-F).
Connection Status: Display whether the reader is online and connected properly.
OSDP Open Relay: Check the door to be opened.
Details: Click to view the card reader’s information.
Power Output Control
The device can serve as a power supply for the external relays. Click here to view power output requirements.
To set it up, go to the web Access Control > Relay > 12V Relay Output interface.
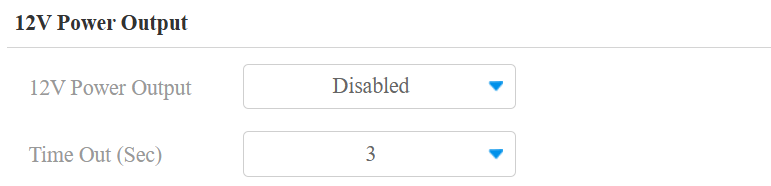
12V Power Output:
Always: Provide continuous power to the third-party device.
Triggered by Open Relay: Provide power to the third-party device via 12 output and GND interface during the timeout when the status of relays is shifted from low to high.
Time Out (Sec): Select the power supply time duration after the relay is triggered from 3, 5, and 10. It is 3 seconds by default.
Integration with Control4
The device supports integration with Control4, which enables users to call, monitor, and open doors on the Control4 panel.
Click here to learn the detailed configuration and other models supporting the integration.
To enable the integration, turn on a switch on the Device > Control4 interface.
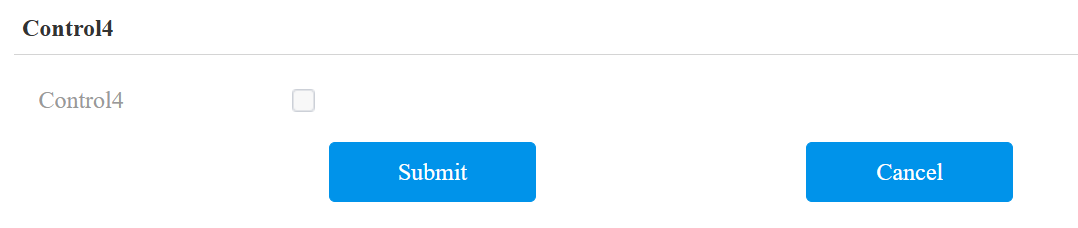
Control4: When enabled, High Security Mode, RTSP Authentication, and Discovery Mode will all be disabled.